All you need for a secure journey
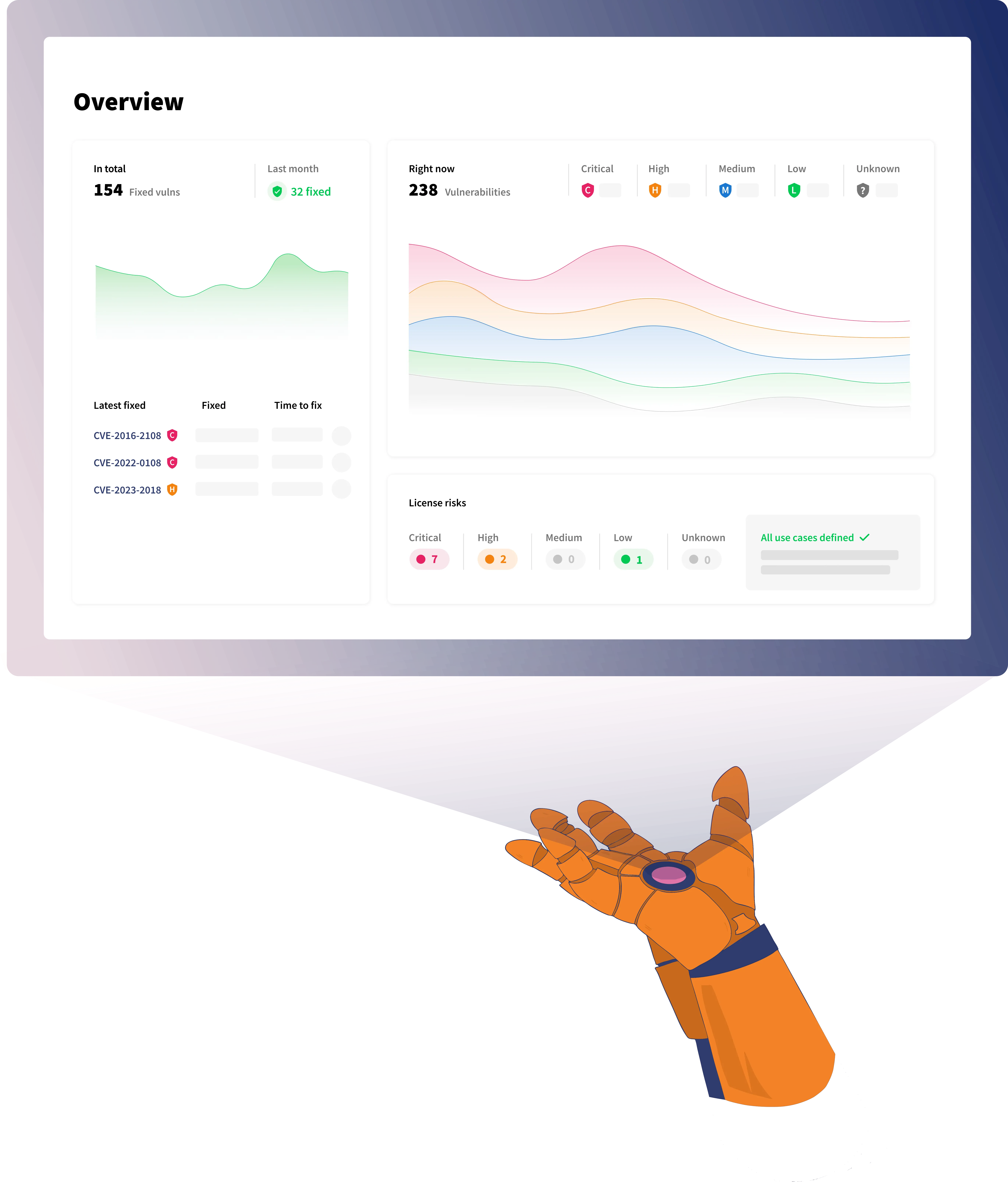
Automate the process of managing vulnerabilities in open source dependencies. Continuously identify, prevent and fix vulnerabilities with a few simple clicks.



SECURITY
Integrate, scan and receive your first results within minutes. Get a full overview of all open source vulnerabilities in your software
EXPLORE DOCSBLOG
Learn more about best practices, new findings and industry news.


Acing your open source vulnerability management – step by step
In this blog post, we will first look at the different steps of vulnerability management and then discuss how Debricked can manage vulnerabilities in open source components.


The importance of protecting your source code and how Debricked can help
The use of open source continues to increase over the years, but many companies have a business model where much of the intellectual property resides in the actual software and its source code.